Sygate® Personal Firewall
CUSTOMER
SUPPORT
Several
troubleshooting options are currently available to Sygate Personal Firewall customers.
- A User Guide is presented below.
- Email and online help
are available at www.sygate.com/support.
- Newsgroup support is
available at news://news.sygate.com.
- Premium telephone
support can be purchased at www.sygate.com/support.
Sygate® Personal Firewall
USER GUIDE
This user guide
has been prepared for Sygate Personal Firewall
customers. A complete copy of the User Guide in PDF
format can also be downloaded from http://www.sygate.com/support/doc.htm.
Overview of Current Security Policy Configuration
Configuring Sygate Personal Firewall
Setting Up a Security Schedule
Application Network Access Policy
Configuring Sygate Personal Firewall in a VPN Environment
Viewing Logs from Previous Days
Understanding Logs Received in Email
Appendix
A Client configuration through initialization file
Appendix B Default Status of Ports and Protocols
Appendix D Useful Information for Advanced Users
Understanding Security Levels
Sygate Personal Firewall has several security settings that you can use to customize your protection when you are connected to the Internet. This chapter will help you to understand the unique structure of our security levels and choose the security level that is best for your individual needs.
Security Level Settings
|
To change your security level, drag the indicator to the desired level. |
|
|
Ultra High: Blocks all Internet traffic.
Use this setting only when you are not using any programs that access
the Internet. This is a good setting
to use for maximum security when you expect to be away from your computer for
an extended period of time. For
information on how to set an automatic scheduler to do this for you, please
see “Setting Up a Security Schedule” in the chapter entitled “Configuring
Sygate Personal Firewall.” |
|
High: Only allows certain protocols such as email, telnet, and Web
browsers to connect to the Internet. This
setting is recommended for most users who connect to the Internet with
popular programs. If you have
problems connecting to the Internet while you are using High Security, switch
to Medium Security while you are using those programs. |
|
Medium: Allows any local Internet applications to communicate with the
Internet. Supports all protocols and
most ports. This level is recommended while gaming on the Internet. |
|
Low: Ideal for accepting inbound Internet requests. This level is
recommended when the computer is acting as a server. |
|
Off: Sygate Personal Firewall provides no protection. |
Sygate Personal Firewall Security Levels are set up in a unique way. When you add a setting to a security level, it automatically adds that setting to the security levels below that security level.
A Setting added to High Security Level Settings
affects these levels:
|
A Setting added to Medium Security Level Settings
affects these levels: |
A Setting added to Low Security Level Settings
affects these levels: |
|
High |
Medium |
Low |
|
Medium |
Low |
|
|
Low |
|
|
To add or remove settings associated with security levels, you must remove them using the security level in the pull down menu to which you added them. There are three Config windows that associate the settings that you add with a particular security level. These are: Advanced Port Settings, Advanced Protocol Settings, and Advanced ICMP Settings.
|
For example, if you add local port 23 to the High Security Level settings, although local port 23 will also be allowed when you use Medium and Low security, it will not show up in the “Open extra local ports” window for these two security level settings. You must choose High security in the pull down menu at the top of the window to see that port 23 is added and you must also choose High in the Security Level pull down menu to remove it. The same rules apply to the Medium Security Level setting. |
|
Overview of Current Security Policy Configuration
A Security Policy is a set of rules that you configure in order to maintain a consistently secure computing environment. In the current version of Sygate Personal Firewall, the Security Policy is made using three different methods:
1. When an Allowed/Disallowed application is added (in Application Network Access Policy), that application is security level independent.
2. When a Trusted IP Address is added, that IP Address is trusted only in the security level specified (security level dependant).
3. When a port, protocol, or ICMP setting is added, that setting applies to a set of security levels as explained above in the Security Level Settings section.
Configuring Sygate Personal Firewall
Sygate Personal Firewall is better than ordinary computer security programs because it can be customized to fit your Internet lifestyle. Sygate Personal Firewall makes it easy to add commonly accessed IP addresses, allow often-used programs to run, and even schedule your computer security level. This chapter covers all the basic features that can be configured in Sygate Personal Firewall.
Notes for Enterprise Users |
|
You may notice that some of the configuration options in the following screens may be grayed out for you. This means that your System Administrator is controlling those settings. If you need to alter settings that are in grayed out areas, you should contact your System Administrator for assistance. |
Click Config to see how easy it is to change Sygate Personal Firewall’s settings.
Setting Up a Security Schedule
This is a useful feature especially for
parents and business owners that want to prevent Internet connections for a
certain time period each day. It also
makes it convenient for you to increase the security level at night, when you
are away from your computer.
|
Click on the Security Schedule tab. This feature enables you to automatically
change the computer’s security level for a particular time of day. Note:
The time must be entered in military time. To convert to military time, use the same numbers as you would
for AM. For PM, add 12 hours. For example, if you wanted to enter 4pm,
you would add 4:00 + 12:00 = 16:00. You can also set ultra high security when
the screen saver is activated. By default these two features are disabled. |
|
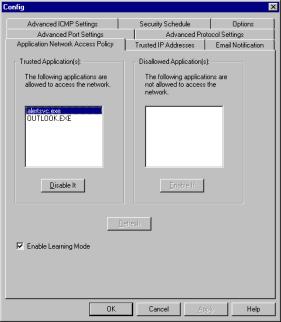
Application Network Access Policy
This tab lets you view
applications that access the Internet and choose to allow them access or disallow
them access to the Internet.
|
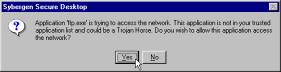
Click on the Application Network Access Policy tab. The left column lists applications that are allowed to access the Internet while the right column lists applications that are denied access to the Internet. If the Enable Learning Mode box is not checked, Sygate Personal Firewall will assume that all applications are allowed to access the Internet. Sygate Personal Firewall will automatically add these programs to the Trusted Applications list. If the Enable Learning Mode box is checked, Sygate Personal Firewall will prompt you with a pop up window for each application that is not in your Trusted Applications box. An example is at the right. If you click Yes, the program will be added to the Trusted Applications list. If you click No, the program will be added to the Disallowed Applications list. Note:
This feature is security level independent, which means that when you
allow/disallow an application, that application is allowed/disallowed in all
security levels. |
|
Trusted IP Addresses
Add IP addresses that you
contact or that contact you often. For
example, if you are at home and want to contact your work machine, add the IP
address of your work machine in this window.
|
Click on the Trusted IP Addresses tab. Currently, Sygate Personal Firewall does not support name lookup, which means that the IP address must be in numeric format. Note: The trusted IP addresses that you enter
are tied to a particular security level.
For example, if you entered 111.22.333.44 to the High Security level,
that IP address would only be trusted while using the High Security
level. If the security setting is
changed to Medium or Low, the trusted IP addresses would need to be
re-entered for that level. Allowing
a Trusted IP address in this window only allows TCP, UDP, and ICMP protocols. |
|
Email Notification
This window lets you set
up an email address for Sygate Personal Firewall to contact in the case of a
security alert. The email that you
receive is simply a text version of the log file (see the chapter on “Logs” for
more information).
|
Click on the Email Notification tab. In the “Email From:” box, enter your email address. In the “Email To:” box, enter the email address of you or your System Administrator. Enter a Subject in the “Email Subject:” box. An example would be “Security Alert.” Enter the numeric IP address of the SMTP server (mail server). If you prefer not to receive email, check the “Don’t Notify” box. If the “Notify Immediately” box is checked, Sygate Personal Firewall will send an email message to you every time that it detects a security alert (indicated by a red X in the log file). If you prefer to be sent a digest of recent logs, check the “After every ___ minutes” box and enter the number of minutes between email messages. Note: This feature is most useful for
administrators who want to monitor a remote machine. For home use, viewing the Logs by clicking
the Logs button on the GUI is recommended instead of receiving logs
through email. |
|
Options
This tab gives you
greater flexibility in tailoring Sygate Personal Firewall to your networking
needs.
|
Click on the Options tab. You can: 1.
Choose how Sygate Personal Firewall
Service starts--automatically at system startup or
manually every time. 2.
Enable
Password Protection so that no one else can change your security settings. 3.
Select
whether you would like Sygate Personal Firewall to generate detail logs or
summary logs. For more information on viewing logs, see the “Logs” chapter. |
|
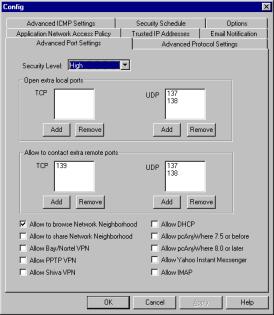
Advanced Port Settings
The Advanced Port Settings window provides
the flexibility to create and customize your own security policies.
|
Click on the Advanced Port Settings tab. This is a useful feature for online game users, who can contact the game developers to find out which ports are used in a specific game, and then customize the security level with those ports. Please see Appendix C for more information
on commonly used ports. There are check
boxes provided for commonly used services such as Network Neighborhood and
Yahoo Instant Messenger. For
additional information on VPN, please see the chapter on “Using Sygate Personal Firewall
in a VPN Environment.” For an
explanation of security levels, please see “Understanding Security Levels.” Note:
Under the High Security Level setting, you can open extra local ports and
allow to contact extra remote ports.
Under the Medium and Low Security Level settings, you can open extra
local ports that are less than 1000 and block local ports that are between
1000 and 65535. For a chart that
lists all defaults (and will help you to understand why the settings are
different depending on the Security Level), please see Appendix A. |
|
Notes for Enterprise Users |
|
If you use a LAN (Local Area Network) for printing and file sharing, you must click the Allow to browse Network Neighborhood check box in order to print files and access the network. In order to share your local files, you must add local tcp port 139. |
Advanced Protocol Settings
A protocol specifies the
rules of syntax with which a message will be transmitted.
|
Click on the Advanced Protocol
Settings tab. Type in the protocols you want to block or
open. Then click OK For more information on VPN, please see the
chapter on “Configuring Sygate Personal Firewall in a VPN Environment.” Please see Appendix C for more information
on protocols. For an explanation on how security levels
work, please see “Understanding
Security Levels.” Note: Under the High Security Level
setting, you can allow extra protocols, while under Medium and Low Security
Level settings, you can block extra protocols. For information on the default status of protocols for each
level and to help you understand why the settings change with the Security
Level, please see Appendix A. |
|
Advanced ICMP Settings
Internet Control Message Protocol (ICMP) is a valuable protocol when troubleshooting network problems.
|
Click on the Advanced
ICMP Settings tab. In Medium and Low security, all ICMP messages are allowed. The most commonly used feature of ICMP is ping. To use ping, you must check the Allow Echo Reply and Allow Echo Request boxes. |
|
|
When you are finished Configuring Sygate Personal Firewall, click OK to exit the Config window and save
your settings. |
Configuring Sygate Personal Firewall in a VPN Environment
A VPN (Virtual Private Network) is used to connect to a network and transfer data securely. All data that travels between machines using a VPN is encrypted. The use of VPNs is exploding as more businesses move their operations onto the Internet. Even small businesses are finding that their customers and suppliers are requiring them to access a VPN to place orders, calculate future demand, or review account billing. To use a VPN with Sygate Personal Firewall, follow the steps below.
Click Config on the GUI.
|
Click on the Advanced Port Settings tab. At the bottom of the window, there are checkboxes for three different flavors of VPN. Check the box of the one you use. If the Security Level is set to Medium or Low, the VPN boxes will automatically be checked. |
|
|
Click on the Advanced Protocol Settings tab. At the bottom of the window, there are two different flavors of VPN listed. Check the box of the one that you use. If the Security Level is set to Medium or Low, the VPN boxes will automatically be checked. |
|
|
Click on the Trusted IP Addresses tab. Add the numeric IP Address of the computer that you want to connect to. If you don’t know the IP Address, change your Log settings to “Detail” under the Options menu. Then try to connect to the IP Address to which you want to connect. Next, view the log file by clicking Logs on the GUI. You should see the IP Address of the computer to which you are trying to connect. Click Add in the window to the right and add that IP Address. Currently, allowing a Trusted IP address in this window only allows TCP, UDP, and ICMP protocols. |
|
Logs
It is useful to view log files not only in order to determine whether or not your computer system has been attacked, but also to troubleshoot problems. Viewing logs also provides you with valuable information about the traffic that is going to and from your computer.
Viewing Logs
The present day’s logs can be
viewed by clicking the Logs button on the GUI. Sygate Personal Firewall offers two types of
logs: Detailed and Summary. Select the type you prefer by clicking
the Config button on the GUI and then clicking on the Options tab. The default is Summary Logs.
|
Summary
Log—Generates logs to show current security status and current Internet
activity, with blocked access attempts highlighted with a red X. |
|
|
Detailed
Log—Generates a log for every network activity (connection) through your
computer to provide additional information, such as port status, TCP sessions
and DNS requests. |
|
For
each log line, the following information is displayed if it is available: 1.
Time:
Time an activity occurs. 2.
Activity:
Description of activity. 3.
Remote IP:
IP or domain name of remote computer. 4.
Remote Port:
Port of remote computer. 5.
Local IP:
IP of user computer. 6.
Local Port: Port of your computer in use. 7.
Direction:
Shows if Internet traffic is inbound or outbound. A red X indicates a message that you should pay particular attention to. This message may alert you to a security attack. |
|
Understanding Log Messages
Some of the log messages may seem cryptic to non-technical users. The table below should help you understand what the log messages mean and help you separate messages that are intended to provide information from messages that indicate a potentially serious security problem.
|
Message |
Meaning |
|
Initiate non-expected TCP connection. |
This a fairly common message that indicates a connection that your computer is trying to make is not expected by Sygate Personal Firewall. This message should be viewed with concern only if you were not using any programs that accessed the Internet when this message appeared. |
|
Starting (Stopping) Sygate Personal Firewall Service… |
This entry lets you know when Sygate Personal Firewall is turned on and when it is turned off. |
|
Service: Start stopping service |
Although this message seems confusing, it is simply telling you that Sygate Personal Firewall is beginning the process of shutting down its security service. |
|
Sygate Personal Firewall service stopped. |
This message confirms that you have turned off Sygate Personal Firewall. |
|
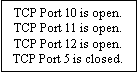
TCP Port ____ is open (closed). |
When you add or remove ports in the “Advanced Port Settings” window, the changes are reflected in the detail log (but not the summary log). For example, if you added ports 10-12 and removed port number 5, your log would report:
|
|
Block (Open) all protocols. |
Block all protocols appears in the log when you have changed your security level to Ultra High security. Open all protocols appears when Sygate Personal Firewall is using medium or low security. |
|
Ultra High (High, Medium, Low) security is active (ready). |
These messages simply remind you which security level you are using. The difference between active and ready is that active means that the security features are actually in use while ready means that Sygate Personal Firewall is ready to keep your computer secure when you connect to the Internet. If you are connected to the Internet all the time, you will usually see only “ready” messages while if you are a modem user, you will see “active” messages when you are not connected to the Internet. |
|
Ping request. |
This is a message that you should watch for. This message could indicate that someone is looking for vulnerable security spots on your computer. If you see a request like this, keep a close eye on your logs for possible security attacks. |
|
There is probably a port scanner attacking this computer. |
If you see this message, you should make sure you keep your security level on High whenever possible since your computer may be a target for hackers. |
Viewing Logs from Previous Days
Sometimes you might want to check previous days’ logs in order to spot trends in connections if you suspect that your machine is being attacked. Sygate Personal Firewall saves each day’s logs in a separate file, making it easy for you to look back on a particular day’s logs. Periodically, it’s a good idea to delete old files that you don’t need anymore. To delete old files, click on the file that you want to delete and press the delete key.
|
On the current Log screen, click the Tools menu and choose Log Viewer. A window with all of your saved log files will appear on the screen. You will see a directory with current archived log files listed in it. The file name is in the form of ‘mmddyyyy.log’ where ‘m’ is for month, ‘d’ for day and ‘y’ for year. Note: The Network Interface option
assists tech support in troubleshooting network problems. Double click on one of the log files. Sygate Personal Firewall will bring up WordPad and let you view the selected log file. |
|
Understanding Logs Received in Email
You can receive email notices that contain security alert messages (those marked by a red X in the logs) either immediately or at intervals (every 30 minutes, for example). For more information on enabling this feature, see the “Email Notification” section of the “Configuring Sygate Personal Firewall” chapter.
|
To the right is an example of the message that you might receive in email. The Subject is determined by you and may be different from the one shown here. “Sygate Personal Firewall Warning Message” will appear at the beginning of the email. Next, each of the messages will appear. In the example to the right, there are two messages. It is easiest to understand the log if you picture each message as one line, as in the Log file window. Read from left to right, each field represents: Time, Activity, Error (ignore this), Local IP, Local Port, Remote IP, Remote Port, and Direction (Inbound/Outbound). If there is no information for a certain field, it will be left blank with ‘’ in its place. |
From:
<user@sygate.com> To:
<myself@sygate.com> Sent:
Wednesday, January 19, 2000 6:12 PM Subject:
Security Alert! Sygate Personal Firewall
Warning Message Fri
Jan 21 14:29:23 2000 '01/21/2000
14:29:23' 'PING request' 'Error' '10.0.3.57' '' '10.0.1.191' '' 'Inbound' Fri
Jan 21 14:36:01 2000 '01/21/2000 14:36:01' 'Initiate non-expected
TCP connection' 'Error' '10.0.3.57' '7323' '10.0.1.191' '106' '' |
Troubleshooting Tip
The
messages in the log file make it easy for you to find programs that conflict
with Sygate Personal Firewall. Follow
these steps to solve most problems:
1.
Make sure Sygate Personal Firewall
is running.
2.
Try connecting
to the Internet with your program/game/service.
3. If it does not work, click the Logs button on the GUI.
Look at the current log and note any information about the program that you just tried to run. Take note of port numbers, protocols, and IP Addresses. Enter that information in the correct window and try your program again. If you still have a problem, check the Troubleshooting chapter for more information.
|
Add Ports Here |
Add Protocols Here |
Add IP Addresses Here |
|
|
|
|
Troubleshooting
Most problems can be fixed by viewing the log file and adding ports, protocols, or IP Addresses to their respective configuration window. For information on using log files to help you debug your problem, please see the chapter on “Logs” for more information.
If you have a problem that cannot be addressed by the information contained in this manual, please view the support web page for additional information: http://www.sygate.com/support.
Problem |
Solution |
|
I have lots of red Xs in my log with “Initial non-expected TCP connection.” |
It means that an unexpected connection has been requested but rejected by Secure Desktop. If this is a legitimate connection request, use the log file to verify the reoccurring port(s) and add it into “Advanced Port Settings.” |
|
I cannot run my application (for example, pcANYWHERE) in High Security level but am able to do it in Medium Security. |
Most likely the requested port(s) is being blocked, however, adding the reoccurring port(s) into the “Advanced Port Settings” window will allow you run your program. In pcANYWHERE 9.0, adding Local TCP port 5631 and Local UDP 5632 will do the trick. See the debugging tip in the “Logs” chapter for more information. |
|
How do I know whether or not Sygate Personal Firewall is really protecting my computer? |
On the GUI, click the Test button (the computer must be connected to the Internet for this to work) to have Sygate Personal Firewall check your machine for security leaks. Also, check the log file to make sure that Sygate Personal Firewall Service is running. |
|
I have Windows 98 Second Edition (or Windows 2000) with Internet Connection Sharing pre-installed. Can I use Sygate Personal Firewall? |
In order to use Sygate Personal Firewall, Internet Connection Sharing (ICS) must be disabled. |
Notes for Enterprise Users |
|
If you use a LAN (Local Area Network) for printing and file sharing, you must click the Allow to browse Network Neighborhood check box (located on the Advanced Port Settings tab) in order to print files and access the network. In order to share your local files, you must add local tcp port 139. |
Sygate Personal Firewall Enterprise Edition requires proper configuration of client initialization options to ensure reliable server/client communication. The initialization options can also be used to establish the initial configuration for Sygate Personal Firewall software. The client initialization options are specified in the Ssd.ini file, which is located in the same directory as the installation files for Sygate Personal Firewall. Using the Ssd.ini file can be a valuable tool when administrating several machines that require the same settings.
It is suggested that system administrators configure the Ssd.ini file prior to Sygate Personal Firewall deployment to ensure consistent communication and security across the network. The following text explains the use and options for each of the Ssd.ini settings.
Note: It is wise to make a backup copy of the original Ssd.ini file before you alter it in case there is an error that you cannot find in your altered version.
Note: 0 means false (or no) while 1 means true (or yes).
|
If you are using Sygate Management Server, then these two lines should have the # symbols removed and appropriate host IP and host name added. If you are not using Sygate Management Server, these two lines should be left alone. This part pertains to the installation of Sygate Personal Firewall. You can specify a destination in which the program will be installed and a folder name where icons, etc. will be placed. The EnableSilentInstall option will allow you to automatically install the program without being prompted. To enable that feature, change the 0 to 1. If you don’t want to be prompted for a trial key, change the 1 to 0 after UseTrialKey=. This is the security setting that will be active the first time you start Sygate Personal Firewall. This section lets you enable Ultra High security for a specified time period each day. Follow the comments in the code to change the settings. This part lets you password protect your Sygate Personal Firewall Settings. Follow the comments in the code to do this. If you want a Summary Log, leave the default as-is, if you want a Detailed Log, change the EnableSummaryLog option to 0. Enabling learning mode will prompt you before each application that requests access to the network is allowed to access the network and will store that information in the Disallowed Applications list. You can manually add Disallowed Applications under the Disallowed Applications heading. By default, applications are allowed. Add Trusted IP addresses, which are tied to each specific security level, here. Add Ports, which are tied to each specific security level, here. Add information between the quotes for each field to be notified about security alerts generated by Secure Desktop. Add Protocols, which are tied to each specific security level, here. |
[SMS] host IP = 10.0.3.166 host name = test004 [Startup] DestinationDirectory="C:\\Program
Files\\sygate\\Sygate Personal Firewall" SSDFolderName="Sygate Personal Firewall" EnableSilentInstall=0 UseTrialKey=1 [SSD] ; Valid values for "Default Security Level" are
Ultra/High/Medium/Low/Off Default Security Level = High [Security Schedule] ;Valid Values for "EnableUntraAtScreenSaver" are 1(means
Yes) or 0(means No) EnableUltraAtScreenSaver = 0 ;Valid Values for "EnableUltraAtTimer" are 1(means Yes) or
0(means No) EnableUltraAtTimer = 0 ;Valid Values for "EnableUltraStartHour" are 0-23 EnableUltraStartHour = 22 ;Valid Values for "EnableUltraStartMinute" are 0-59 EnableUltraStartMinute = 0 ;Valid Values for "EnableUltraEndHour" are 0-23 EnableUltraEndHour = 8 ;Valid Values for "EnableUltraEndMinute" are 0-59 EnableUltraEndMinute = 0 [Options] ;Valid Values for "EnablePassword" are 1(means Yes) or
0(means No) EnablePassword = 0 ;Valid Values for "EnableSummaryLog" are 1(means Yes) or
0(means No) EnableSummaryLog = 1 [Application Network Access Policy] ;Valid Values for "EnableLearning" are 1(means Yes) or
0(means No) EnableLearning = 1 [Trusted Applications] [Disallowed Applications] [High Trusted IP] [Medium Trusted IP] [Low Trusted IP] [High Advanced Ports] ; All the variables in this section values either 1(means Yes) or
0(means No) EnableNetworkNeighborhoodAtHigh = 1 EnableBayNortelVPNAtHigh = 0 EnableYahooInstantMessengerAtHigh = 0 EnableDHCPAtHigh = 0 EnablePPTPVPNAtHigh = 0 EnableIMAPAtHigh = 0 EnablePCAnyWhere7.5AtHigh = 0 EnablePCAnyWhere8.0AtHigh = 0 [Medium Advanced Ports] ; All the variables in this section values either 1(means Yes) or
0(means No) EnableNetworkNeighborhoodAtMid = 1 EnableBayNortelVPNAtMid = 0 EnableDHCPAtMid = 0 EnablePCAnyWhere7.5AtMid = 0 [Low Advanced Ports] ; All the variables in this section values either 1(means Yes) or
0(means No) EnableNetworkNeighborhoodAtLow = 1 EnableBayNortelVPNAtLow = 0 EnableDHCPAtLow = 0 EnablePCAnyWhere7.5AtLow = 0 [Email Notification] ;Valid value is either 1(means Yes) or 0(means No) EnableNotification = 0 ; Valid email address kept in a string EmailFrom = "" EmailTo = "" EmailSubject = "" ; Valid value is the IP address of email server like 255.255.255.255 EmailServerIP = "" ;Valid value is an integer, 0 means immediately EmailNotifyInMinutes = 0 [High Protocols] ; All the variables in this section values either 1(means Yes) or
0(means No) EnableBayNortelVPNAtHigh = 0 EnablePPTPVPNAtHigh = 0 EnableICMPAtHigh = 0 [Medium Protocols] ; All the variables in this section values either 1(means Yes) or
0(means No) EnableBayNortelVPNAtMid = 1 EnablePPTPVPNAtMid = 1 EnableICMPAtMid = 1 [Low Protocols] ; All the variables in this section values either 1(means Yes) or
0(means No) EnableBayNortelVPNAtLow = 1 EnablePPTPVPNAtLow = 1 EnableICMPAtLow = 1 |
Appendix B Default Status of Ports and Protocols
Security Level |
Default Settings
|
||
|
|
Allowed Protocols |
Inbound1 |
Outbound2 |
Ultra-High
|
None |
None |
None |
|
High |
TCP & UDP |
None |
FTP (20,21) Telnet (23) Email (SMTP+POP3) (25,110) DNS (53) HTTP (80) Secure HTTP (443) |
|
Medium |
All |
1000 – 65535 (for TCP & UDP) |
All |
Low
|
All |
For both TCP & UDP: FTP (20,21) Telnet (23) Email (SMTP+POP3) (25,110) DNS (53) HTTP (80) NNTP (119) Secure HTTP (443) 1000-65535 |
All |
|
1. Local computer ports accessible from
other computers. 2.
Remote
ports accessible from the local computer. |
|||
Appendix C FAQ
Can a Sygate Personal Firewall user use
DHCP?
Yes. To enable this feature:
1. click Config on the GUI
2. click on the Advanced Port Settings Tab
3. click the “Allow DHCP” check box
4. click OK
Are there any limitations for AOL users?
High security level is not available for AOL users.
Are there any limitations for NT users?
High security level is not available for NT dialup users.
Can I use InternetPhone, NetMeeting, ICQ,
and pcANYWHERE?
Yes,
you can use InternetPhone, NetMeeting, and ICQ in Medium security and
pcANYWHERE in High security.
How do I uninstall Sygate Personal Firewall?
The safest and most effective way of uninstalling Sygate Personal Firewall is to use the uninstall utility provided with the software. To do this:
Click on StartàProgramsàSygate Personal FirewallàUninstall Sygate Personal Firewall
By using this method, Sygate Personal Firewall installer will not only remove related Sygate Personal Firewall files but also registry keys
How can I clean up the Sygate Personal Firewall log file?
To delete any log file, delete it using Windows Explorer or drag it into the Recycle Bin. It is highly recommended that you clean up the log file periodically.
Can I still play games after Sygate Personal Firewall is installed on my computer?
Yes,
you can play games in Medium security mode. We tested the following games in
Medium security mode: Quake II, Diablo, Age of Empires, and Ultima.
Appendix D Useful Information for Advanced Users
Commonly Used Ports and Their Corresponding Protocols |
||
|
Service |
Port |
Protocol |
|
DNS |
53 |
UDP |
|
HTTP |
80 |
TCP |
|
HTTPS |
443 |
TCP |
|
SMTP |
25 |
TCP |
|
FTP |
21 |
TCP |
|
FTP-DATA |
20 |
TCP |
|
POP-3 |
110 |
TCP |
|
IMAP |
143 |
TCP |
|
TELNET |
23 |
TCP |
For a complete guide to ports, protocols, and other networking information, please see this website: